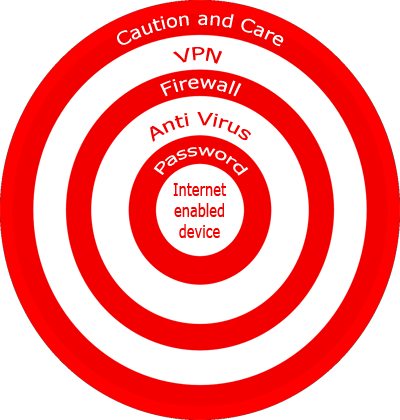
Said nobody with an understanding of the Internet ever.
No one and I really mean no one is safe from identity theft. The degree and seriousness of the impersonation depends largely on how soon it is detected. Also how determined and efficient the criminal has been.
Steps that can be taken to limit the possibility and likelihood, but as I have said nobody is exempt. Even famous personalities and showbiz stars have fallen victim. Steve Jobs co founder of Apple famously had his identity stolen admittedly in a parody blog, but just goes to show.
Rather than re invent the wheel, here are some links to some of the most horrendous and bizarre instances of recent years. Some truly devastating tales that are literally jaw dropping.
| Four Scary Identity Theft stories |
| Somebody took over my life |
| Robbed of over $265,000 over four months |
| Man wrongly branded as a paedophile |
| Retired nurse fleeced |
If you want to protect yourself, check out out out Self-Help page, or if you would like to talk to us about how we may help, or enquire about an ongoing maintenance and security arrangement, please use the contact link at the top of the page, or click here.

| Follow @speeednet |